The short version: “It varies”.
“Have you applies the latest security fixes from your operating system vendor to your machines?” I asked, trying to a learn a little more about Fred’s security posture.
Fred replies with hesitation, “We apply security patches every three months. The last time we deployed fixes was … um … two-and-a-half months ago.”
I scratched my aching head and said, “Two major buffer overflow attacks were released last week.”
- From the first edition of Counter Hack by Ed Skoudis, and very outdated.
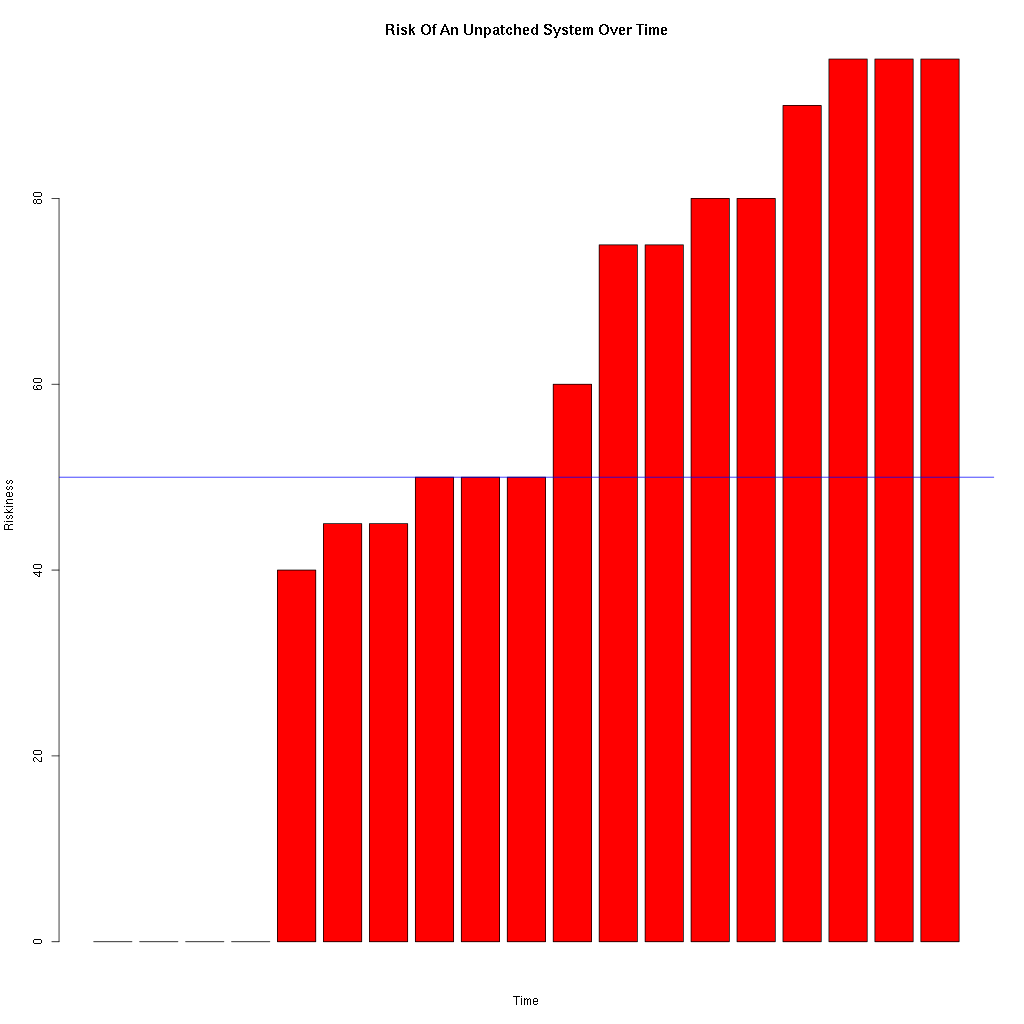
Applying operating system patches to a system reduces the known risk associated with the operating system to zero, but that known risk starts increasing the moment the system finishes it’s final post-patch reboot. The risk might increase very quickly or very slowly, but the increase in risk looks something like …
You might choose to patch when the level of risk reaches 50, but to do so you will need to assess the level of risk associated with every security vulnerability that each patch fixes. And that level will vary on the nature of the vulnerability, and the nature of the server in question.
As an example, a patch that fixes a privilege escalation vulnerability that requires an authenticated account to work with can be assessed as being very low risk for a server that is not widely available (i.e. no Internet access). Whereas the risk assessment for a server that is open to the Internet, and has a very large number of accounts that can authenticate, should be very high.
However carrying out a full risk assessment for each server on the network, and for each patch that is released would be exceptionally expensive.
As an alternative we resort to patching every N days where N is a balance between the risk of known security vulnerabilities, and the disruption to the business of patching. Of course if the disruption of patching is exceptionally damaging to the business, ways to design the infrastructure that allows for patching without disruption should be pursued.
Looking at how long N can be, there is no value of N that is safe. Even if you patch every day, there is still a small window of opportunity when an attacker may succeed. All we can do is reduce the risk.
So is patching every three months sufficient? Well it is better than not patching at all, but no security professional could possibly say that it is sufficient without risking being accused of professional misconduct. And yes there will be occasions like that given in the quote at the top where patching every three months will allow an attacker in.