It may have reached your attention that there was a significant denial of service attack against a widely used DNS provider – the service provider for organisations such as Twitter, Github, and Amazon. The effect was to make certain services unreachable leading some to believe that the Internet was down!
Some of the major links may provide additional information :-
- https://www.hotforsecurity.com/blog/ddos-attack-against-dns-provider-knocks-major-sites-offline-16977.html
- https://www.youtube.com/watch?v=AsEzDXjyhG8&feature=youtu.be
- https://www.flashpoint-intel.com/mirai-botnet-linked-dyn-dns-ddos-attacks/
The details of the attack are still being disclosed, but it appears very likely that a widely known ‘bot army of compromised “Internet of Things” devices was used to perpetrate a simplistic denial of service attack against Dyn DNS. Specifically their DNS infrastructure in the US which may or may not have been a specific Dyn DNS customer.
As a result, their DNS infrastructure was clobbered and because many sites chose a very short caching value, the names disappeared off the Internet.
This sort of attack could be mitigated in a number of ways (not all are realistic or possible) :-
- Dyn DNS could increase their defences against denial of service attacks. Which I am sure they are doing – they already had defences, but not sufficient for this level of attack.
- People who run DNS for their company should consider increasing the amount of time the names are cached for. If the Dyn DNS servers disappear off the Internet, it won’t be as noticeable if the values they would have returned are already cached elsewhere.
- IoT manufacturers should pay far greater attention to the security of their devices. Most IoT customers are not likely to have sophisticated IT professionals available to deal with security updates.
- ISPs should look at blocking traffic from infected machines to prevent denial of service attacks. There is always the argument that the average customer of an ISP isn’t sophisticated enough to know that his Internet connected curling-tongs are joining into a co-operative effort to blast a DNS server into rubble, but there does come a point where being nice to the naive needs to take second place to protecting the Internet as a whole.
To get a quick peek under the curtain of the problem, let’s take a look at the size of the problem we see here. For October so far, we have denied :-
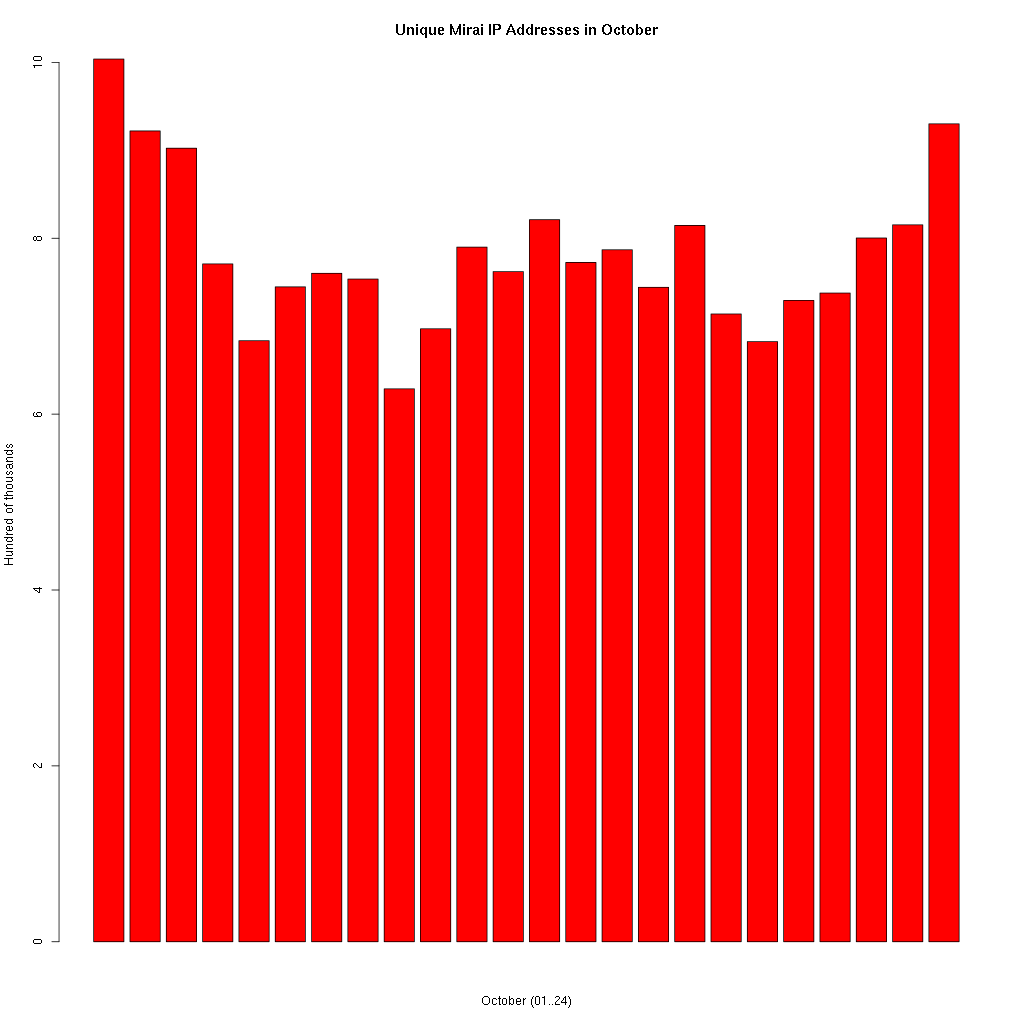
Each of those bars represents a single day in October, and the height corresponds with the millions of connection attempts we have blocked. Individual infected devices (cameras or DVRs apparently) is making many connection attempts of course, the following shows the number of unique devices making telnet connections (don’t be confused by the scale – it’s hundreds of thousands so the peak is approximately 1 million) :-
This is a big problem.