The following is the analysis of a real phishing attack that we have seen, together with some indications of how a phishing attack can be detected. For the impatient, some of those indicators are listed below :-
- Are you expecting to receive a document from the person sending it? You may want to check back with them to be sure they really intended to send it.
- Don’t open suspicious attachments, but if you do, does it contain something sensible? Sending a PDF document containing a link to a shared cloud storage folder doesn’t actually make sense – the link could be contained within the original email.
- Are there inconsistencies in the words? For example does the message mention Google Drive, but the link say Dropbox?
- Don’t follow suspicious links contained within suspicious attachments, but if you do, and it takes you to a Google logon screen :-
- Are you already logged into Google? You shouldn’t need to re-authenticate that quickly.
- Does it actually look like the Google logon screen? It might look similar but are there differences?
- Does the location bar (where your browser shows the address of the current page) mention Google? If it doesn’t, back away from the page slowly.
- Does the location bar contain a green padlock? If it doesn’t, your login credentials won’t be encrypted which is very suspicious.
And onto the analysis …
A number of people received an email “from” someone at the University containing a PDF attachment together with a suggestion that it contained something worth reading. Opening the attachment from a previously unknown correspondent and with an oddly worded email was the first mistake.
If you do receive such attachments, it is worth checking with the sender to see if it is legitimate.
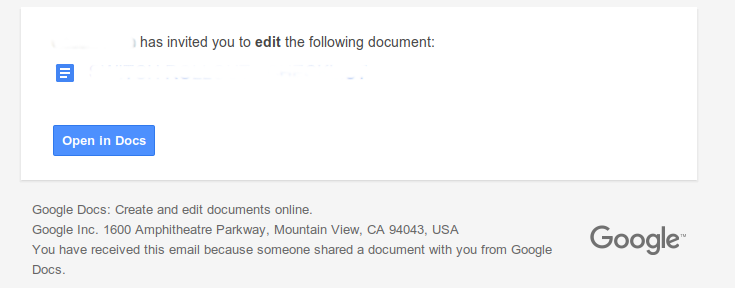
If you do make the mistake of opening it, the first odd thing to notice is that the attachment is named “Scan…” but contains content that obviously isn’t scanned :-
So if this is a google drive document, why isn’t it being shared in the normal way? Which looks more like :-
(I’ve erased the name of the sharer and the name of the document)
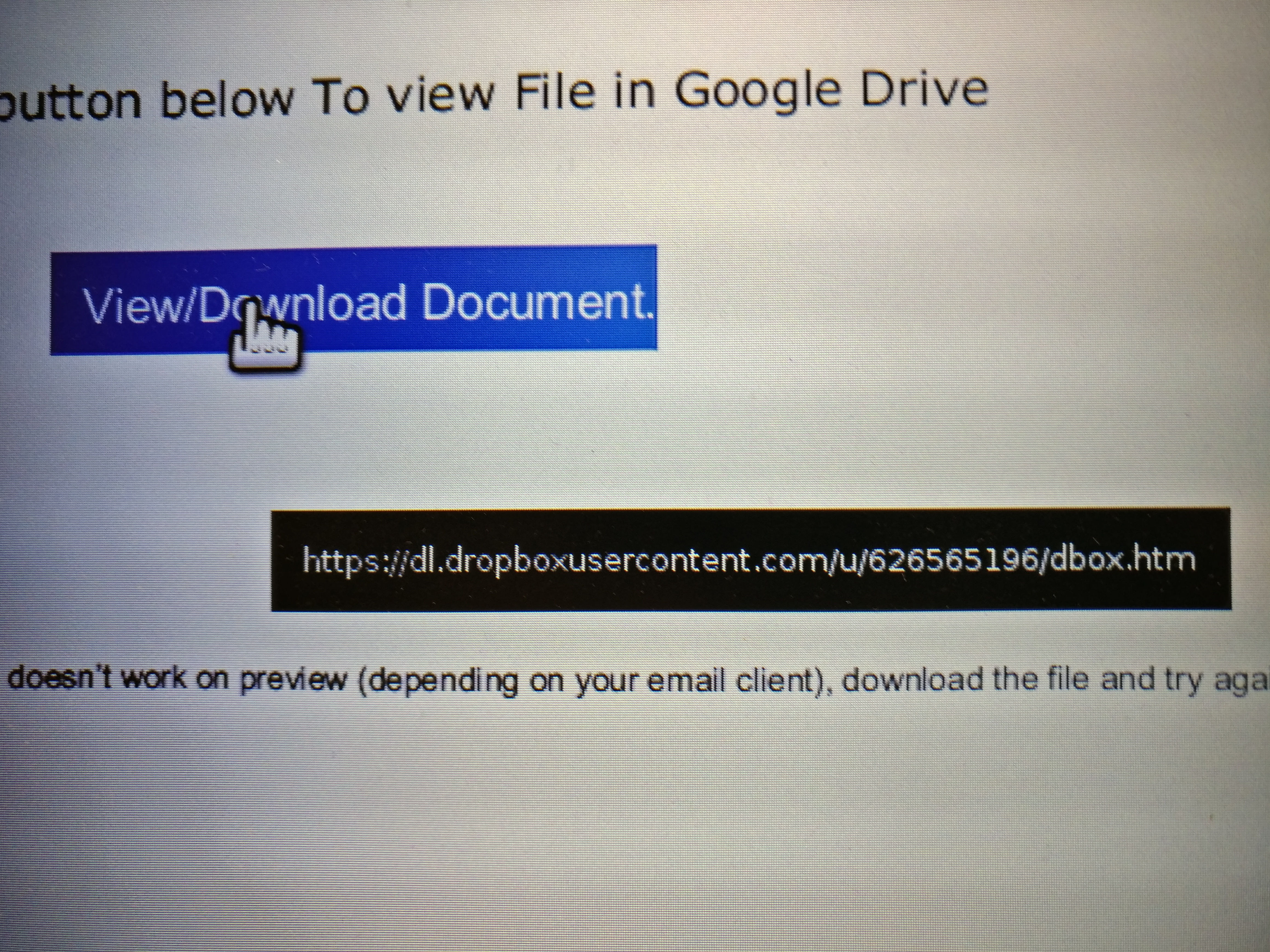
In addition, if you hover your mouse over the button you get a pop-up with the link address in :-
So the text says “Google Drive” and the link says “Dropbox”? Another suspicious indication.
If you download the link from Dropbox (in a controlled manner!), the “document” is actually a web page with a base64 encoded content (with a page title of “Zeuxhaxor” (if that doesn’t look suspicious to you, your suspiciousness needs tweaking)) that sends you onto another web page hosted at http://freecabin.net/.
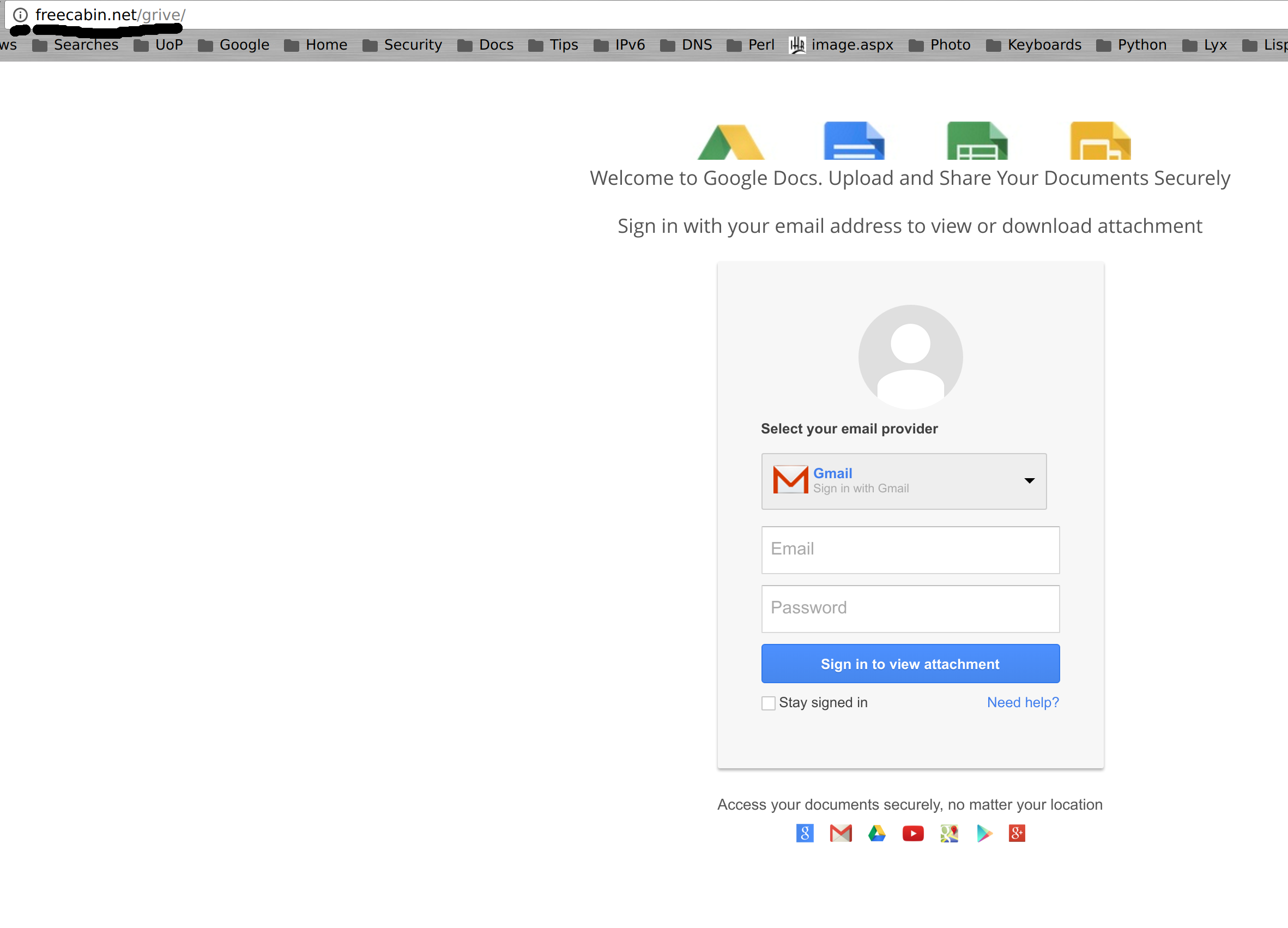
If you visit the page, you end up faced with the following (without the hand-drawn lines) :-
This also has plenty of indications that something is wrong :-
- Aren’t you already logged into Google? Why do you need to login again?
- Look at the location bar (where the two black hand drawn lines are): Why is the address “freecabin.net”?
- Look at the location bar again: Where is the green padlock you would see on a secure page? Do you really want to send out your username and password insecurely?
Phishing attacks are intended to dupe you into leaking your username and password combination, and as such the attacker tries to make things look as authentic as possible. However there are usually many small signs that something is wrong – at least wrong enough to check with someone before you leak your account details.