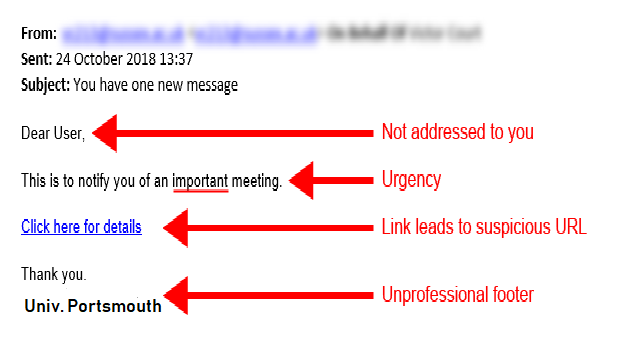
I have just been alerted to yet another phishing attack that works by sending web links via email to a “secure message” (or in the example no words at all). The link of course takes you to a malicious site that will try and fool you into disclosing your credentials.
The latest attack will look something like :-
There may well be minor variations (or major ones).
As usual :-
- If the email is from someone you do not know, be cautious about the contents.
- If the email contains a link for you to click on, point at the link and check what the real destination is. If you do not know how to do this, you can right-click on the link, select “Copy link address” or “Copy link location”, and then paste the clipboard into an empty text message – it will look something like “https://secure.mailmsg-43.host/….”.
- If the email is “from” someone you know and the language looks odd – unusually illiterate (or unusually literate), strange spellings, etc. then check “out of band” (i.e. via another way of communicating) that the message is legitimate.
- If an email asks you to do something unusual – in particular bypassing normal procedures – then check with someone else to see if it is legitimate or not.