There has been lots of stories relating to two new severe security vulnerabilities (one of which is in every Intel processor for over a decade); the trail of stories starts here. The details of the vulnerability are very highly technical so this post will concentrate on the less technical aspects.
As the original papers highlight, this is a result of a decades long policy across the industry of increasing complexity in pursuit of performance over security.
What Is Vulnerable?
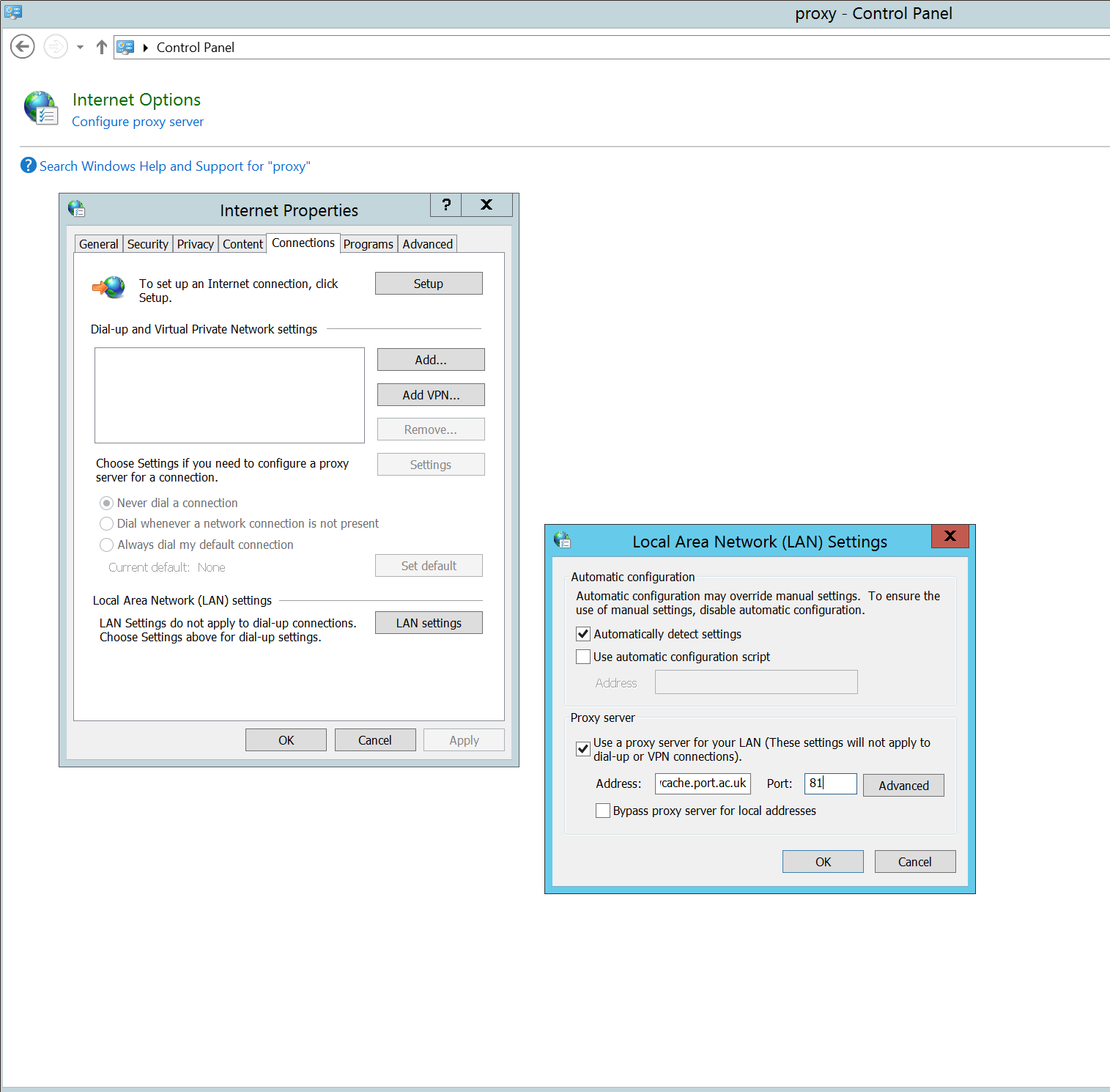
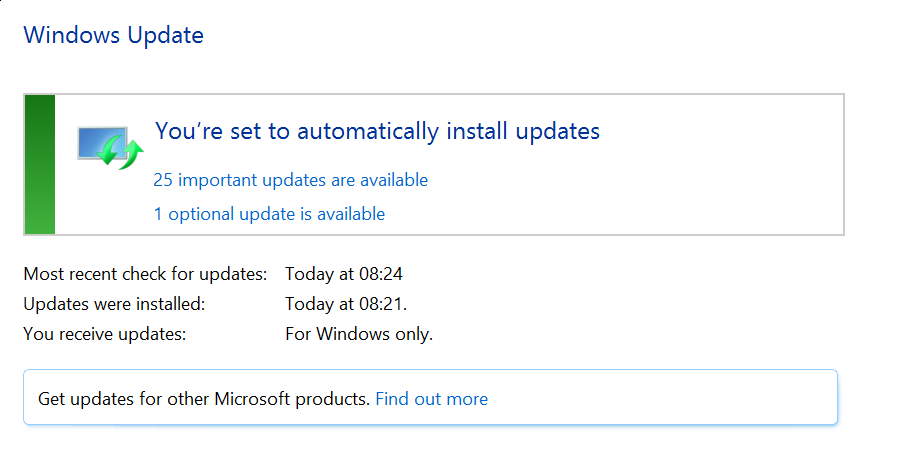
For Meltdown, practically everything with an Intel processor; it is known that patches for Linux and Windows are being prepared. macOS was patched in December (if you have patched recently!).
Information on the vulnerability of other processors to Meltdown is a bit varied at present. It may be that AMD processors are vulnerable under certain conditions (although AMD have claimed that they are not vulnerable).
It is probable that Spectre is effective on rather more processors – AMD, and possibly some ARM processors (smartphones).
What Is The Effect?
In short, this is unknown. Technically Meltdown allows an attacker to access parts of kernel memory from any user process. This by itself sounds not so bad, but it allows an attacker to defeat defenses that have made whole classes of old attacks no longer viable. Essentially in combination with other attacks, the machine can be totally compromised.
In the case of Spectre, the effect is to be able to use the same sort of side-channel to view data from other processes address spaces, and in addition to escape “sandbox restrictions”. This means data leakage.
However this requires an attacker to be in control of data that controls the execution path through the victim’s code. Which is generically a hard thing to do, although in some cases (browsers) it is likely to be quite easy. Expect browser (and other application) patches to be released shortly … and apply them!
What Does The Meltdown Patch Do?
With the rumour that the the Meltdown patch causes a performance hit of 5-30%, there is some concern over it.
Technically the Meltdown patch is a work-around for the problem – it moves the kernel address space out of the user address space. Every time a system call is made, the processor has to reload the memory management unit, which takes time. Thus the performance hit.
How exactly this will effect performance remains unknown to a certain extent. Essentially applications that make very heavy use of system calls will notice a performance hit, and those that don’t will probably not notice a hit. In terms of desktop applications, it is likely that the web browser will be hit, but most other applications are likely to be unaffected.
It is likely that servers will notice the effect the most, and it is likely that only on heavily loaded servers will the effect be noticeable.
Summary
This is a serious set of vulnerabilities, and there is a significant risk of those vulnerabilities being used. In addition the mitigation for Intel processors has a significant risk of causing a performance issue.
However there is no reason to panic – patches are currently being prepared for release or have been released already.
There are many sources of information on these vulnerabilities being published; not all of which can be assumed to be totally correct (this posting included).
Links to further information :-