The following is one of a number of spam messages that I received yesterday; all carefully filed away in the spam folder.
To Whom It May Concern, Please find attached an invoice relating to Penalty Charge Notice Number IA54236946 along with a copy of the contravention. In order to prevent this fine from escalating further we have paid this fine on your behalf. Should you have any queries concerning these charges please don’t hesitate to contact me. Payment for this invoice will be taken by Direct Debit 9 working days from the date of this email. Please refer to page 2, point 3.6 in your Terms and Conditions for information on Traffic Offences. Regards, Buddy [invoice54236946.doc application/msword (23129 bytes)]
If you received something similar (and you probably did), the following may be of some interest.
Of course it was a spam message, and of course the attachment was a malware payload (which would not have been detected by the majority of anti-virus engines). The interesting thing (and an opportunity to demonstrate something) was that many of us will have received a number of copies.
I saved 14 copies of the attachment (don’t try doing this unless you really know what you are doing), and all were different. The files were all multi-part MIME files containing a JavaScript and a binary. The binaries were all different.
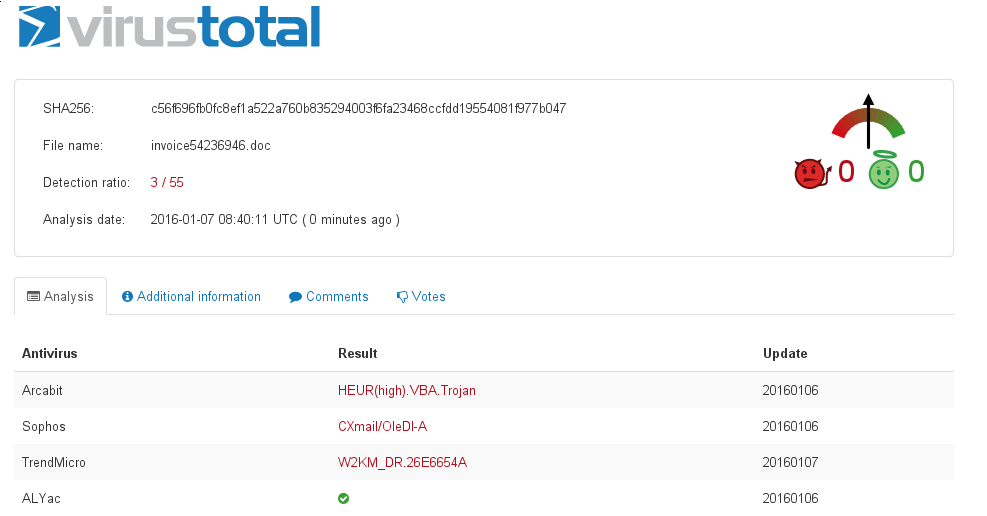
Loading one of them into VirusTotal revealed only 3 AV products detected malware :-
Three on the day after; on the day itself it was only two.
This illustrates several things :-
- Malware writers are still attempting to infect computers with nothing more sophisticated than click-to-infect where you rely on someone doing something less than clever.
- Malware writers are producing malware that morphs per message. It is possible that this invoice malware has a different binary signature for every single copy that was sent out (and it was probably millions sent out).
- Anti-virus products don’t detect this malware at the initial stages (a 5% detection rate is small enough to say “don’t”).