Those keeping aware of the security scene may well have become aware of the latest ransomware worm hitting around the world. Various names have been associated with this outbreak, and the most readily identifiable name (Petya) is technically incorrect.
This is a classic ransomware infection with the added bonus of the ability to cross-infect machines on the local network using both the vulnerability that WannaCry exploited (“ETERNALBLUE”) and another Windows vulnerability that allows an attacker (or a piece of malware) to execute code on a target computer using compromised account credentials.
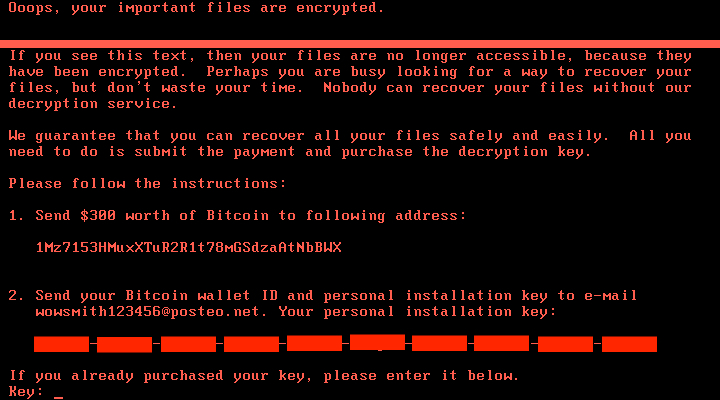
Once infected, the ransomware stays hidden whilst it starts encrypting files. This example also forces a reboot after an hour at which point it displays an information page :-
At this point it is too late (especially as the address wowsmith123456@posteo.net has been shut down). Paying to decrypt your files is unlikely to be effective (and is unethical).
Now for the good news :-
- It appears that this spreads through local networks and not via the Internet.
- It is probable that the initial infection occurs through a compromised update to a piece of Ukrainian tax software.
So in all likelihood, we are relatively safe from this infection.
However ransomware is incredibly disruptive when it performs a cross-infection like this or WannaCry and it seems likely that this kind of incident will be repeated. So we have to expect to be targeted in the future.
Whilst we already have protection in place, and will be looking to increase those protections, there are no guarantees that a widespread ransomware infection will not strike us.
For further information there are numerous sources of information – the first in the list are relatively light in terms of technical content :-