People are constantly trying to get your account details in one way or another. One of the ways is to simply ask you to tell them your account details. And one of the most common ways of asking is to send you an email asking you to follow a link to download an attachment, or that they’ve shared a Google drive with you.
One of those phishing emails came into me over the weekend, and I followed the link to see the results :-
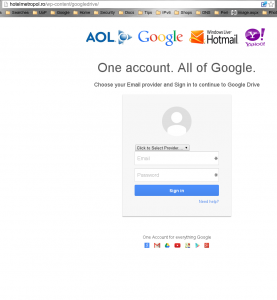
There are a few hints about this web page that indicate that all is not right :-
- It looks a bit like a Google login page, but there’s a drop down box to select which email provider you use.
- The page is just a little bit too busy to be a Google page.
- Since when does Google let people access a Google drive without a Google account?
Lastly, and most significantly, the URL the page is at is all wrong. The following is cut from the above page to highlight the location bar :-
For those who are not aware, the location bar shows the URL of the current page and there is quite a bit to tell from it :-
- Right at the beginning of the location bar is a page icon. The one that is showing is just the default, and Google always uses a little blue “g” on every unencrypted web page.
- And of course Google is not going to let you log in through an unencrypted web page – their log in pages have a little green padlock instead of the default icon.
- The first part of the URL determines the Internet address of the server, and “hotelmetropol.ro” isn’t an address that Google would use.
- Even more technically, the part after the server address (“/wp-content/googledrive/”) includes a pathname (“wp-content”) that indicates the presence of WordPress. Which Google isn’t going to be caught using; and even if they did, they wouldn’t reveal it.
Phishing attacks are getting more and more subtle, but even a relatively sophisticated attack like this one has signs to indicate that not is all as it seems. If you have any reasons to be suspicious of something like this, use another means of contacting the person who sent you the link.