The mainstream media has been spreading reports about Operation Tovar so it is worth expanding on that information.
Operation Tovar is an international co-operative effort by various anti-crime agencies to take down the Zeus-P2P command and control servers. Whilst valuable, it is expected that the criminal gang that runs the Zeus-P2P malware will shortly (perhaps in two week’s time) establish new command and control servers, so taking action now to isolate and clean-up infected machines would be very valuable.
Various efforts are under way, and we will be taking action ourselves.
The first question to ask, is just how does a criminal get control of your PC? In the case of ZeuS, the criminal sends out spam with an infected attachment. The “hook” to persuade people to click on the attachment is to claim the attachment is an invoice or a voice-mail message from someone you know. So the very first defence is to be very suspicious of emails with any attachments.
The Zeus-P2P network is a huge network of compromised machines mapped by Dell :-
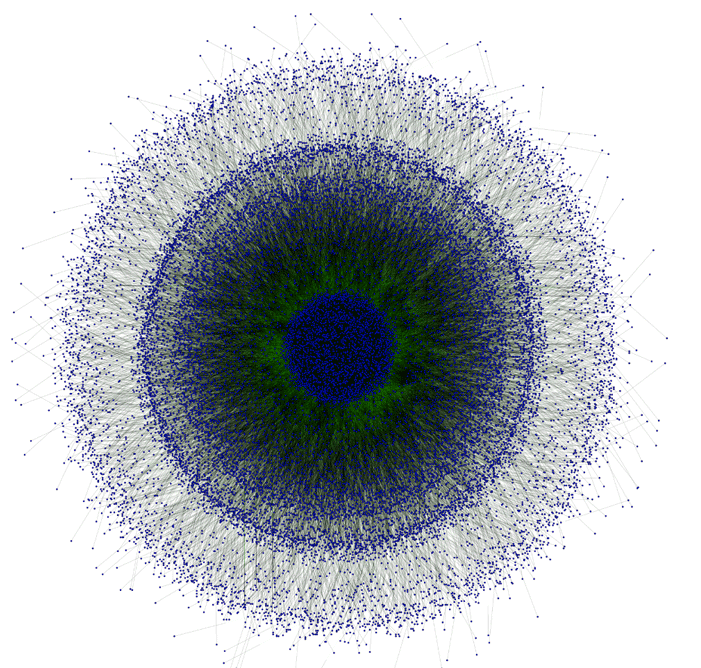
ZeuS P2P Network
Each of those blobs is an infected machine. The network is used by criminals to steal money themselves (one estimate is over $100 million from US victims alone) plus is hired out to other criminal gangs for nefarious purposes. Including the gang that came up with Cryptolocker which is a particularly nasty bit of malware that encrypts your file and refuses to unlock them until you have paid off those who released CryptoLocker.
The number of infected machines out there is an indication that people are not defending their machines properly.
The action taken by the relevant legal authorities has been to target the criminal gangs involved, and have taken down the command and control servers. In combination with that, a number of other organisations have initiated an effort to attempt to persuade people to clean up their infected machines.
What We Are Doing
In the case of centrally managed University computers, the likelihood is that none are infected. Whilst such machines do get infected, the built-in defences normally remove the infection before it becomes effective. In almost all cases where network activity by viruses has been reported, the infection has not been a centrally managed University computer.
In the rare cases where it was a centrally managed University computer, the virus was only able to activate for a short period. Most accounts lack “administrator” rights, so the virus was not able to make it’s presence permanent.
In some ways this is a bad thing, as it does not encourage the first line of defence.
In addition, we have been provided by JANET with a large list of domains that is used by ZeuS and/or CryptoLocker to block. This has been put in place, and should make it less likely that either of these two infections will successfully activate on our network.
Protection
As mentioned previously, the first line of defence against viruses is to be less trusting of emails with attachments – invoices, voice-mail messages, pictures, videos, etc. If you do get an email with such an attachment, make sure it is from someone you definitely know or do business with.
The second defence is to have an anti-virus product installed and kept up to date – we often see people who don’t bother at all, or who installed an anti-virus product once years ago and have not checked that it is still working. Now would be a good time to check that you have anti-virus installed on your personal computers, and that it is still working.
The next level of protection is to run an anti-virus removal tool on your PC such as the Sophos Anti Virus removal tool. Anti-virus products are not infallible (in fact if you pick a bad one they are very fallible), and it makes sense at a time like this to run the removal tool to see if there is anything that has been missed.
For more information:-
- Our National Crime Agency.
- The “KrebsOnSecurity” blog posting on the issue.
- The US Department of Justice.
- The US-CERT list of resources.
