This post is a bit more technical than the usual, and covers a kind of attack that is not only the kind of attack we may fall victim to, but an attack that we could participate in! Defences against this sort of attack are difficult, but avoiding the risk of participating in the attack is far easier.
You could argue that there is no real benefit to the organisation in avoiding participating in attacks as we are not the real victims in such circumstances; however it is (and has always been) considered to be ethical behaviour to avoid causing problems for others on the Internet. And of course the University wishes to be an ethical organisation!
When an attacker wishes to perform a denial of service attack against a victim, there are several possibilities, but one of the common varieties is to simply overwhelm the victim with as much traffic as possible. This is achievable with a simple denial of service attack if the attacker has access to more resources than the victim.
However for an attacker to overwhelm a victim with more resources, they will have to use a distributed denial of service attack where they use the resources of many computers and networks to flood the victim. This is commonly performed using a collection of compromised machines (a botnet), but there is another option …
If the attacker can :-
- Forge network traffic so that it appears to be from the intended victim.
- Make use of a service that will respond to such traffic with an answer to a question that is much larger in size than the question.
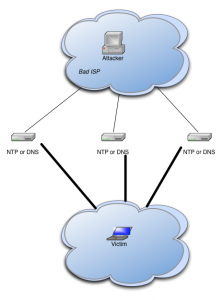
Then the attacker has themselves a viable attack. A simple illustration of this most simple form of this attack appears below :-
As you can see, I have labelled the attacker’s ISP as “Bad ISP”. This is because unless the ISP allows for forged network traffic, then the attack cannot get past the first hurdle. It has long been best practice to block forged traffic (see BCP38), and yes we do.
Unfortunately there are vast numbers of ISPs out there who do not block forged traffic.
Once an attacker has access to a poorly configured network that allows them to forge the source address in network packets, then they have to find the next step – a service that can be used to amplify the attack. The essentials of such a service are :-
- That it responds to a small question with a large answer. This gives the amplification factor that multiplies the amount of traffic that the attacker can send.
- That it is based around UDP rather than TCP. Although TCP can be used in such attacks, it is very much more complicated and hasn’t been used as yet. UDP is simpler as there is no negotiation involved.
- It is also helpful if the service is “light-weight” in that it can easily handle very large numbers of questions and answers.
As it happens two very widely used services – DNS and NTP – are ideal for this kind of attack. If they are configured in a naive manner, the attacker can use them to amplify attacks considerably.
To simplify things I have left out some additional details. The attacker is likely to use a large collection of compromised machines to send the questions to the naively configured services. This increases the amount of denial of service traffic enormously … if an attacker has 1,000 compromised machines and the amplification factor is 10, then 1,000 streams of 1Mbps turns into an attack of 10Gbps.
Most initiatives to combat such distributed denial of service attacks concentrate on fixing the naive configuration of applications, although fixing the “bad” ISPs would solve a whole class of different attacks. As an example, the DNS amplification attack has been known about for ages, but the NTP amplification attack has only recently been used.