If you have not heard, Twitter suffered some sort of incident recently (yesterday at the time of writing) where a number of high profile accounts were used to send out “tweets” suggesting that if you pay them some money (in bitcoin) they would return double the amount of money in bitcoin.
Twitter claims that the accounts themselves were not compromised leading us to the possibility that Twitter has (or had) a vulnerability that allowed anyone to send out tweets as anybody on Twitter – even high profile accounts with blue ticks.
There are several aspects of this story worth learning from.
Firstly, this was one of the classic “wave money to overcome suspicion” attacks – if something is too good to be true, it probably is. At the very least, you will want to check such a strange offer.
Secondly this used prominent Twitter accounts to spread their message – trying (and in some cases succeeding) to abuse an existing trust relationship. We need to be wary of uncritically trusting well known people – we assume that when a tweet appears from a well known individual that they’re the ones actually doing the typing. This isn’t always the case – even in ordinary circumstances – and when a social media giant has security vulnerabilities, that message could be from any criminal.
If a well-known person says something out of character, that message should be viewed with suspicion.
Third, this scam used bitcoin as a payment method. Whilst bitcoin has legitimate purposes, it is also widely used by criminals as the “money” doesn’t go through banks. Any mention of bitcoin should lose a touch of credibility to any message – in combination with other factors could be the deciding factor.
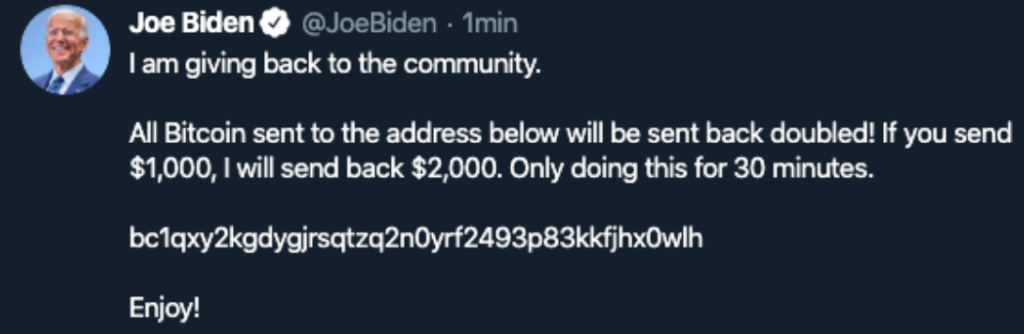
Lastly, look at the “Only doing this for 30 minutes” … anyone tries to rush you into a decision, and they’re quite possibly up to something that you should spent some extra time thinking about.
It is not any one thing that protects us, but a combination of indicators that tip the scales of suspicion into distrusting a message.
