Microsoft have released a whole bunch of patches to fix security vulnerabilities this Tuesday (which is quite normal of course), but one unusual aspect was the release of a patch for older versions of Windows that do not normally get patches.
Which is a bit of an indication that this vulnerability has the potential of being a bit more serious than the usual – Microsoft does not release patches for mostly unsupported operating systems simply when that operating system is vulnerable, but when there is the potential for mass outbreaks potentially causing network-wide disruption.
On the other hand, when the more excitable members of the security community start jumping up and down shouting “It’s Armageddon”, we do have to take their assessment with a pinch of salt.
It is potentially very serious and worth prioritising mitigation measures, but there is no obvious indications that any active exploits are out there in the wild. As yet.
The Links
- Microsoft’s page on the vulnerability (and links to the patch) for operating systems not normally supported).
- Microsoft’s more general page on the vulnerability (and details about patching later operating systems).
The Vulnerable Operating Systems
If you are running one of the following operating systems, you should not only install the patch but also make immediate plans to upgrade – nobody is issuing patches to protect you; patches are release to protect the Internet from you!
- Windows XP
- Windows Server 2003
(And yes, some people do still run such operating systems; in fact I do myself although they are on isolated networks for penetration testing purposes)
If you are running one of the following operating systems, you should install the patch and make plans to upgrade soon.
- Windows 7
- Windows Server 2008
- Windows Server 2008R2
What Is Vulnerable?
RDP (Remote Desktop Protocol). Which is a means of connecting to a Windows machine remotely – very frequently used for server management. Which you may very well think that it doesn’t effect Windows desktop installations, but it can be turned on (and sometimes is).
If it is vulnerable, an attacker can run their own code remotely as the user SYSTEM (which is even more privileged than the Administrator user). But more specifically :-
- RDP without Network Level Authentication (which is not on by default): An attacker can run their code without credentials.
- RDP with NLA: It has been reported that this is only vulnerable if the attacker has valid credentials. That does not mean it should not be fixed urgently however!
- RDP gateway: Some organisations run a single exposed RDP gateway through which people can proxy RDP connections to machines on the inside. I’m not aware of any clear statements whether these are vulnerable or not.
Balancing the probability of exploits being attempted, the probability of the RDP gateway product being exploitable, the impact of a compromise, and the impact of withdrawing the service, IS has blocked access to our RDP gateway – it is only used by a handful of special case users and the VPN is a viable alternative.
Is It Being Exploited?
Probably not. At least not just yet.
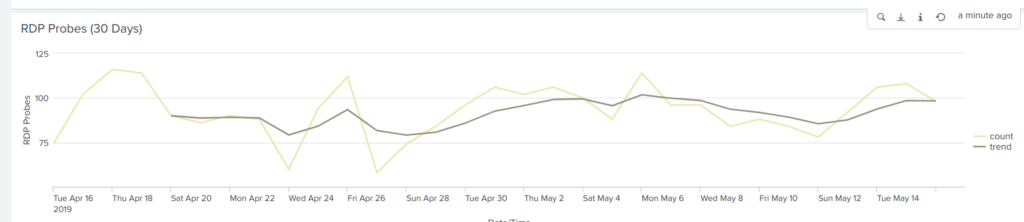
The graph above (which came out a bit smaller than expected) is the number of RDP probes against my home network. The faint line is the count of probes; the darker line is a trend line (exponential moving average which might not be the right one to use as my statistical neurons are very rusty and make a horrible grinding sound when I crank them into life).
Although there is an increase over the last couple of days, it isn’t dramatic enough to indicate anything other than either random variability or an increase in scanning for open RDP ports by security researchers (whitehats, greyhats, and blackhats).
The analysis of the University firewall logs shows much the same kind of activity except for a particularly aggressive scan for about an hour (which itself isn’t indicative of an active attack). However the analysis wasn’t as pretty.
The absence of signs indicating some active attack may well lead some to believe this was a bit of a false alarm, but it is too soon to say that for sure. Example code to exploit the vulnerability is supposedly out there.
It is also worth pointing out that WannaCry (a huge ransomware attack in 2017) made use of a vulnerability that was released into the public domain months before the attack, and the vulnerability was patched by Microsoft a month before the attack. So attacks could come tonight, next week, or next month.
