We are just about to enable something that will email people when there is a critical firewall alert relating to an attempted exploit.
During normal web browsing activity (although not when the web site is encrypted with https), the firewall keeps an eye on the “stuff” that is coming back from the web site. If it spots an attempt to exploit your web browser, it will block it, and log the details into the firewall logs.
We are then post-processing the firewall logs to send out these alerts.
What Should I Do With One?
First of all, don’t panic. You do not have to do anything if you receive an alert.
The firewall has blocked the attempted exploit, and the likelihood is that unless you are running an outdated web browser it wasn’t likely to work anyway. Of course if it was an attempted exploit against Adobe Flash, or Java, then it could well have worked if the firewall had not blocked it.
The alert is simply a mechanism to let you know that the firewall has protected you. It’s also an indicator that letting outdated software (web browsers, plugins like Flash and Java) loose on the Internet is going to lead to tears.
But I Keep Getting Them
In normal circumstances, just about anyone can expect the occasional alert from the firewall. If you keep getting alerts day after day (you shouldn’t get more than one alert per day!), then it may well be worth seeking advice because the level of alerts is unusual.
Amongst other things it may well be worth spending some time getting acquainted with security advice – if you’re getting attacked more often than is commonly the case, it makes sense to find out about protection.
What Is The “ANGLER Exploit Kit” ?
By far the most common vulnerability the firewall is blocking (at least to desktop machines; servers see a whole different bunch of exploits) is the various versions of the “ANGLER Exploit Kit”.
This is a particular version (i.e. it is sold by one particular gang of criminals) of a web-browser exploit kit. When you make a connection to a web server that has the ANGLER exploit kit installed, it will respond with various tuned attacks against your browser – so if you are running Internet Explorer, it won’t bother using Chrome vulnerabilities, and if you have Flash installed it will try to exploit that.
Essentially there are thousands of different ways of exploiting a vulnerability in your browser’s execution environment, and an exploit kit makes it easier for criminals to pick the right set of exploits to try against you.
Once it has successfully exploited your browser it will probably try to get your browser to download some more malicious malware that will persist on your machine, spy on what you are doing, and leak your banking credentials up into the cloud.
But the firewall has blocked it.
How Can I Protect Myself At Home?
At work, the firewall protects you (except if the web site is encrypted with https). But at home?
There are two methods you can use to protect yourself at home. If you are engaged with work activities, there is lot of sense using the VPN (see http://ithelp.port.ac.uk/questions/433/ for instructions). With the VPN turned on, all your Internet activity will go via the firewall (wherever you may be), so you will gain the benefit of the added protection of the UoP firewall.
If that is not an option you are comfortable with, then you can look at more conventional methods of protection, which are detailed below.
Check Your Anti-Virus Protection
Although not a guarantee of protection, having anti-virus protection on your PC is certainly a last level of defence against getting infected with something nasty. It is not just a matter of having an anti-virus product installed, you should also periodically check that it is still healthy and getting updates.
It is not unknown for people to not be aware that their antivirus subscription has lapsed and they are not getting updates. How do we know this? Because such people get infected.
Different antivirus products operate differently, but if you happen to be using Windows Defender (built into Windows 10), then hit the Start button, search for Defender, and then run “Windows Defender” (which should appear in the search results).
You should then be able to get to a screen looking like :-
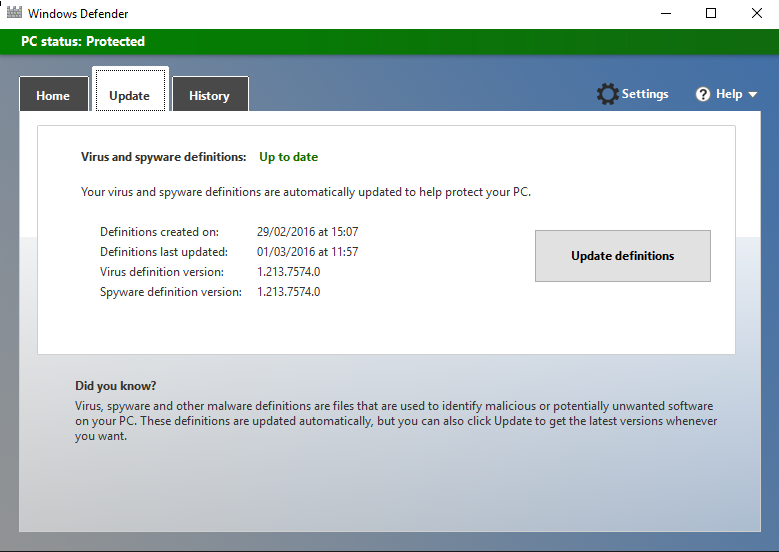
As long as the “Definitions last updated” field reads as the current day, then updates are being applied.
Is Your Browser Updated?
The very first avenue of attack for an Internet hacker is the browser you are using. If it has not been updated recently, then it is almost certainly vulnerable to being exploited. Recent versions of browsers try to update themselves automatically, but automatic things go wrong occasionally!
For details of updating browsers see the relevant link below :-
But I Need IE6 For …?
If you require an ancient web browser version for a particular site (such as your bank), then there are two recommendations :-
- Contact your supplier and complain about having to use an insecure web browser.
- Use your ancient browser only for the site in question; use a modern browser for everything else. It’s perfectly possible to run more than one web browser; even at the same time!
Flash: Just Say No, or at Least Opt In
The Adobe Flash plugin is the attackers weak spot of choice at the moment. It seems to be riddled with vulnerabilities and rarely a week does not go by without a firewall content update to combat Flash vulnerabilities.
The extremist solution to this problem is to remove the Flash plugin, but there are all those sites that still insist on using Flash for interesting (or fun) content. There is an intermediate level of protection you can use (at least with Chrome).
To do this, find Chrome’s Settings menu item, click on the Show Advanced option, scroll down to Privacy, click on Content Settings, and scroll through the pop-up until you see the settings for Plug-ins :-
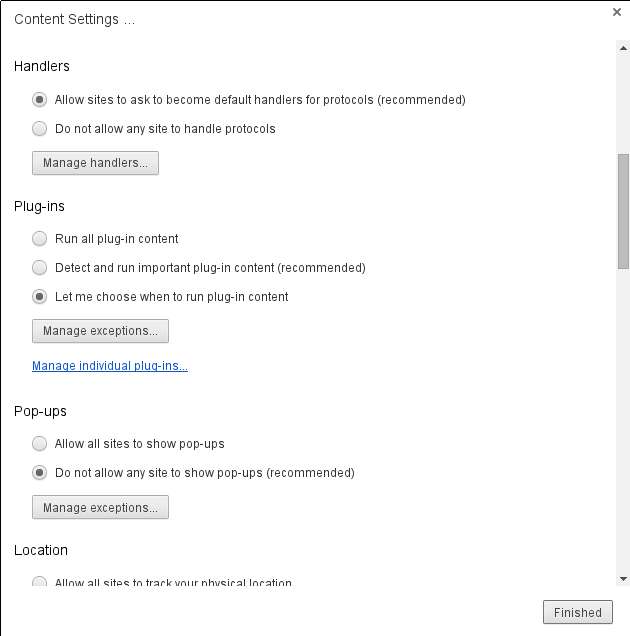
Select the “Let me choose when to run plug-in content” and then the Finished button. Once enabled, flash content will appear on a web page like the following :-

If you want to enable the plugin for a particular part of the page, move the mouse pointer into the relevant area and right-click. The menu that appears will have a “Run this plug-in” item to select. Once selected the content will be downloaded and run.