We are seeing an increase in the number of compromised accounts due to various forms of attack, and decided to highlight some core protections for your account. If your account is compromised, you may find yourself locked out of the account at an inconvenient time (Google does this automatically), find yourself sending huge quantities of spam, or more serious repercussions.
So it is well worthwhile sticking to at least some but preferably all of the following safety tips :-
- Use a long and strong password for your account.
- Do not share passwords – neither with other people nor with other sites. Your ebay account should have a different password to your University account.
- Avoid using your University username on other sites. If one of the other sites is compromised and the account details leaked, it can look like your University account is also compromised.
- Enable two-factor authentication.
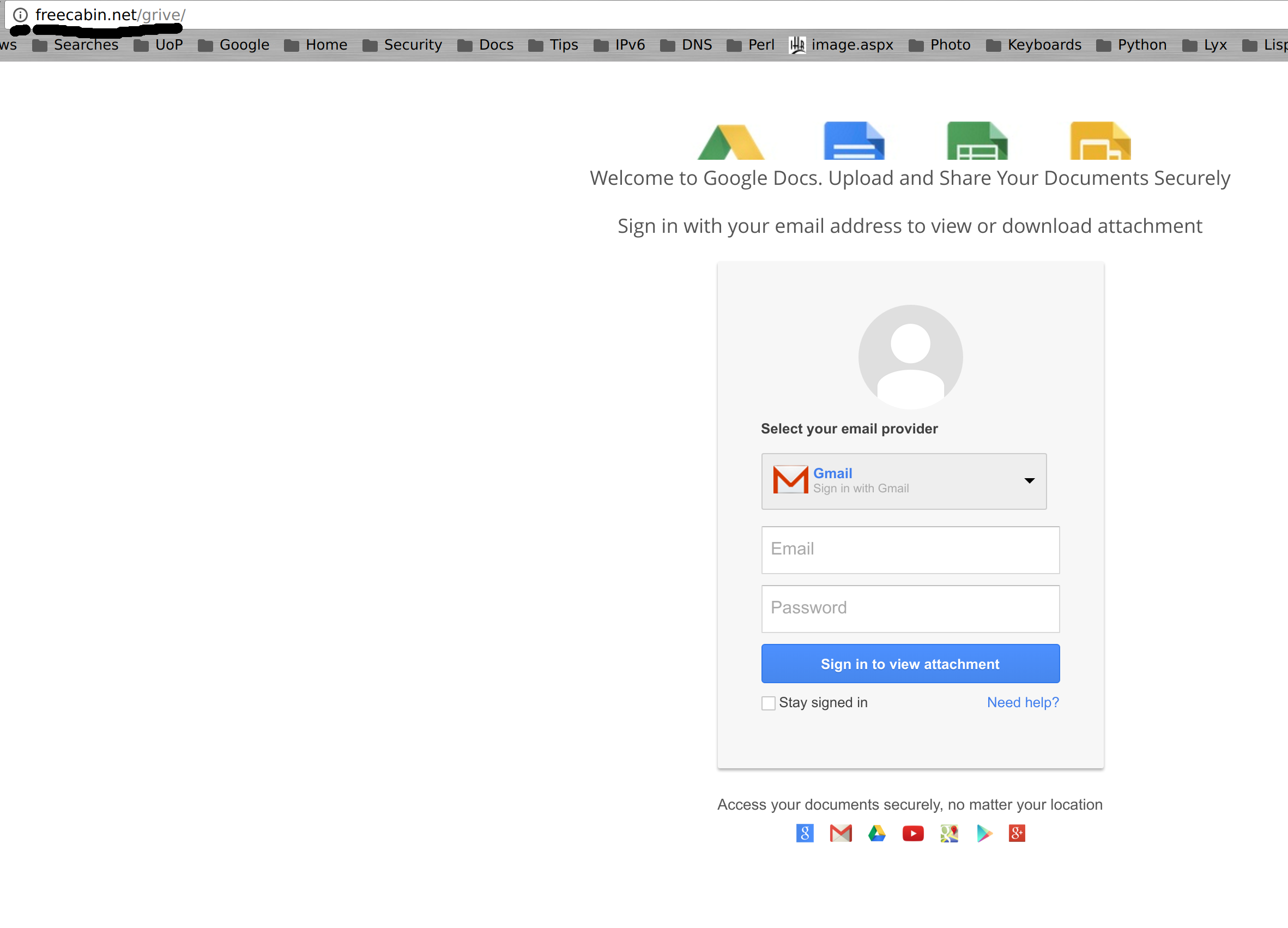
- Be wary of entering your account credentials into a web-based form. You of course need to authenticate to use Google (for example), but you need to be sure it is actually Google asking for authentication.
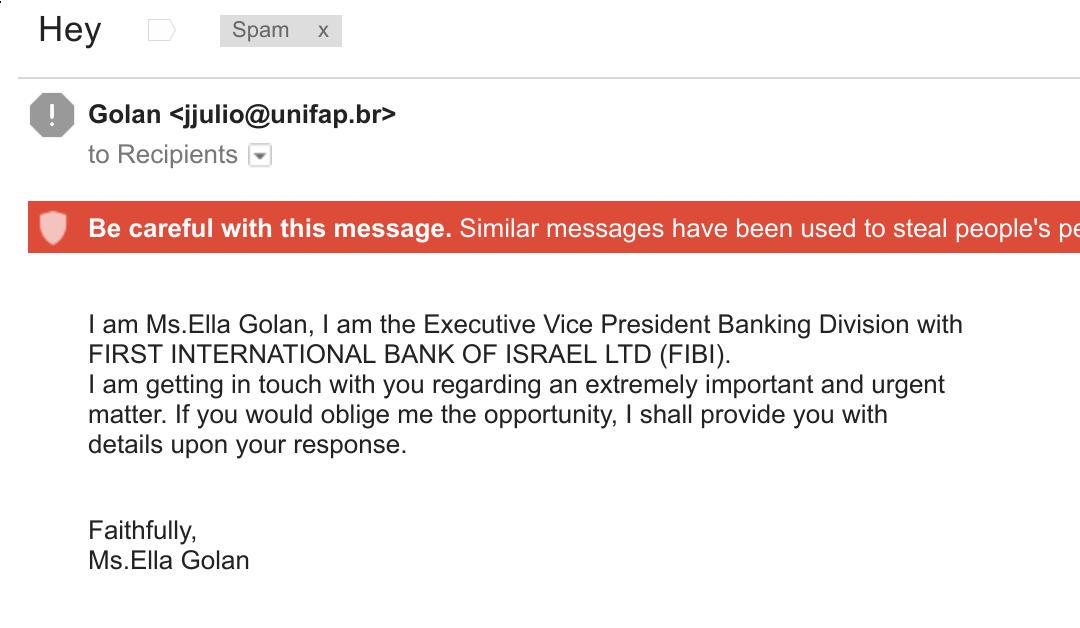
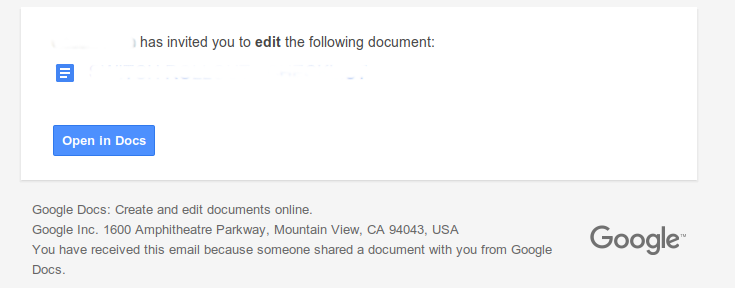
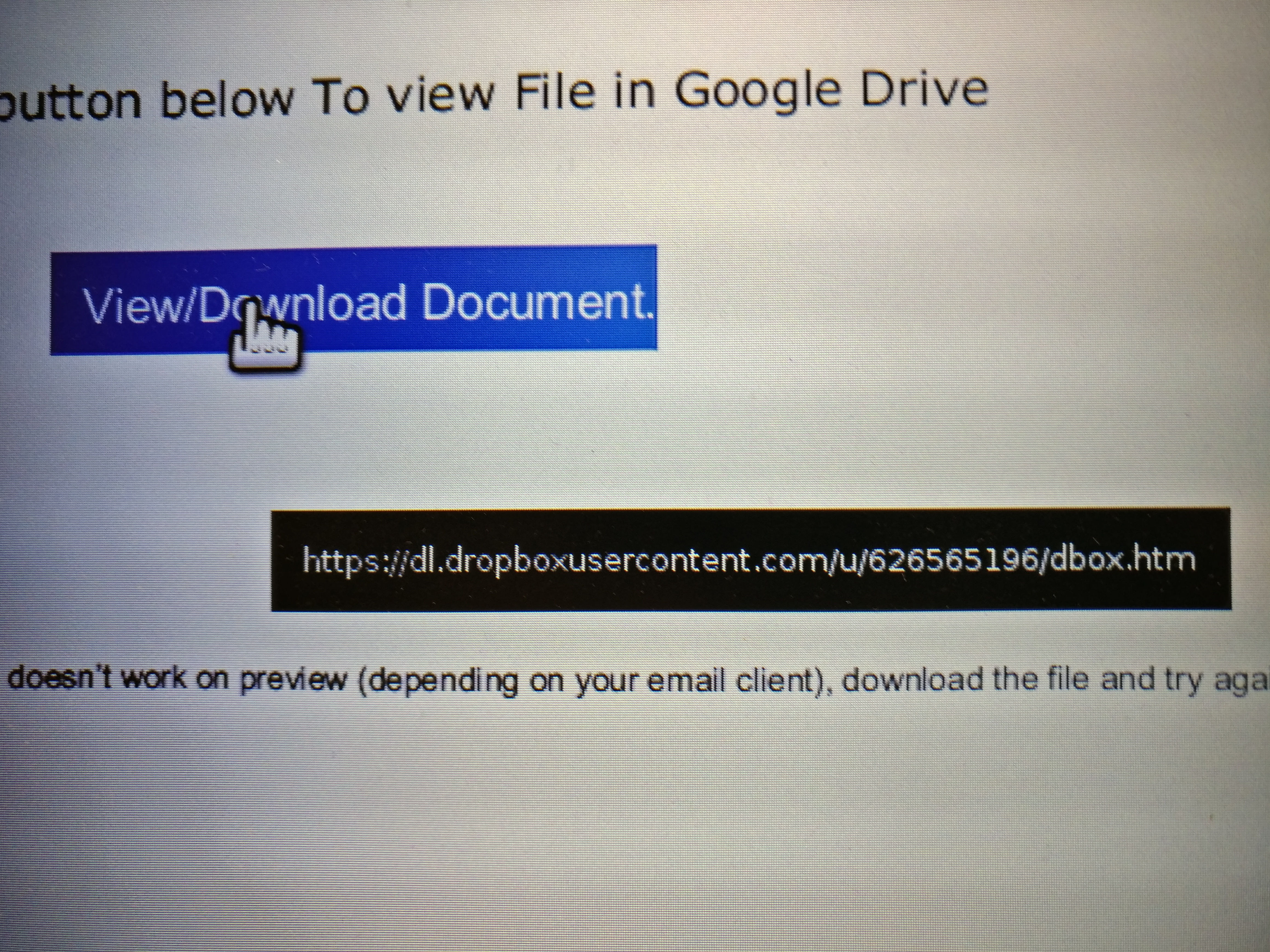
- Don’t follow email links and enter your account credentials. In fact be very careful about following links in email full stop. And yes that applies to trusted correspondents too – once someone has their account compromised, one of the first things to occur is the attacker will use their account to email a form to everyone asking them to login.